The Deceptive Allure of Fake Windows 10 Updates: A Comprehensive Guide to Protection
Related Articles: The Deceptive Allure of Fake Windows 10 Updates: A Comprehensive Guide to Protection
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to The Deceptive Allure of Fake Windows 10 Updates: A Comprehensive Guide to Protection. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Deceptive Allure of Fake Windows 10 Updates: A Comprehensive Guide to Protection

The digital landscape is constantly evolving, with new technologies and threats emerging at an alarming pace. One such threat is the proliferation of fake Windows 10 updates, designed to exploit unsuspecting users and compromise their systems. These deceptive tactics, often disguised as legitimate updates, can lead to significant security breaches, data loss, and financial harm. This article delves into the intricacies of fake Windows 10 updates, providing a comprehensive understanding of their modus operandi, potential risks, and effective countermeasures.
Understanding the Deception: How Fake Updates Work
Fake Windows 10 updates are designed to mimic legitimate updates from Microsoft, often employing sophisticated techniques to appear authentic. They typically leverage the following strategies:
- Exploiting Trust: These updates leverage the inherent trust users place in official Microsoft updates. The appearance of legitimacy, often achieved through mimicking official logos, branding, and download sources, can lull users into a false sense of security.
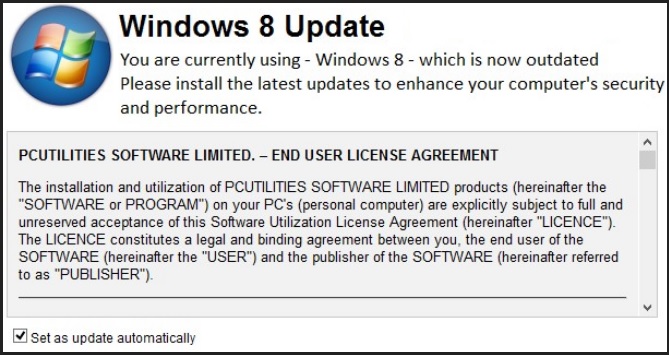
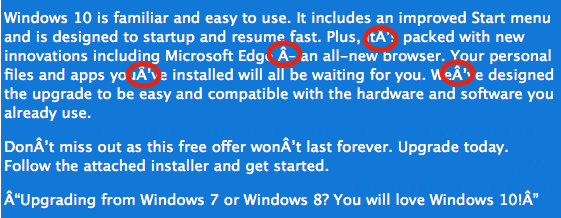
- Social Engineering: Fake update campaigns often employ social engineering tactics, using fear-mongering or urgency to pressure users into installing malicious software. Common tactics include warnings of impending security threats, fake system errors, or claims of enhanced performance benefits.
- Phishing Attacks: Fake updates are frequently distributed through phishing emails, malicious websites, or compromised websites. These sources may contain links that, when clicked, redirect users to download fake update installers.
- Exploiting Vulnerabilities: Some fake updates exploit known vulnerabilities in older Windows versions, allowing attackers to gain unauthorized access to systems. These vulnerabilities are often targeted by attackers who seek to install malware or steal sensitive data.
The Consequences of Falling Prey to Fake Updates
The consequences of installing fake Windows 10 updates can be severe, ranging from minor annoyances to significant financial losses. Some potential risks include:
- Malware Infection: The primary objective of fake updates is often to install malware on the victim’s system. This malware can range from adware and spyware to ransomware and trojans, each capable of causing significant damage.
- Data Theft: Once installed, malware can steal sensitive data such as login credentials, financial information, and personal documents. This data can be used for identity theft, financial fraud, or other malicious purposes.
- System Instability: Fake updates can corrupt system files, leading to instability, crashes, and data loss. This can render the affected system unusable, requiring costly repairs or data recovery services.
- Loss of Privacy: Malware associated with fake updates can monitor user activity, track browsing history, and collect personal information, compromising privacy and potentially exposing sensitive data to unauthorized parties.
- Financial Loss: Ransomware, a type of malware often delivered through fake updates, can encrypt user data, rendering it inaccessible. Victims are then forced to pay a ransom to regain access to their files, resulting in significant financial losses.
Identifying Fake Updates: Recognizing the Warning Signs
Being vigilant and recognizing the warning signs of fake updates is crucial in protecting your system. Here are some key indicators to watch out for:
- Unfamiliar Sources: Be wary of updates downloaded from sources other than the official Microsoft website or trusted software repositories. Avoid downloading updates from suspicious websites or links shared through emails or social media.
- Lack of Digital Signatures: Legitimate Windows updates are digitally signed by Microsoft, ensuring authenticity and integrity. If an update lacks a digital signature, it is likely a fake.
- Incorrect File Extensions: Genuine Windows updates usually have file extensions like ".exe," ".msi," or ".cab." Be cautious of updates with unusual file extensions, as they may indicate malicious intent.
- Suspicious Content: Pay attention to the language used in update notifications, website content, or emails. Fake updates often contain grammatical errors, misspelled words, or inconsistencies in branding.
- Urgency and Fear-Mongering: Be skeptical of updates that claim to be urgent or that warn of imminent security threats. Legitimate updates are typically released with a clear explanation and without unnecessary pressure.
Protecting Your System: Effective Countermeasures
Several preventative measures can be taken to mitigate the risks associated with fake Windows 10 updates:
- Keep Your System Updated: Ensure your Windows 10 system is up-to-date with the latest security patches and updates released by Microsoft. This will help protect your system against known vulnerabilities exploited by fake updates.
- Use a Reputable Antivirus: Install and maintain a reputable antivirus program on your system. Antivirus software can detect and block malicious files, including those associated with fake updates.
- Be Cautious with Email Attachments: Avoid opening email attachments from unknown senders or suspicious sources. If you receive an email claiming to be from Microsoft, verify its authenticity by contacting Microsoft directly.
- Use a Firewall: Enable your system’s firewall, which acts as a barrier between your system and the outside world, preventing unauthorized access and blocking malicious traffic.
- Verify Website Authenticity: Before downloading updates, double-check the website’s URL and ensure it is the official Microsoft website. Look for HTTPS encryption (indicated by a padlock icon in the address bar) to ensure secure communication.
- Avoid Clicking Suspicious Links: Be cautious about clicking links in emails, messages, or social media posts, especially those claiming to be from Microsoft. Verify the link’s authenticity before clicking.
- Be Aware of Social Engineering Tactics: Recognize the tactics employed by fake updates, such as fear-mongering, urgency, or claims of enhanced performance. Do not fall prey to these tactics and always verify information before taking action.
Frequently Asked Questions (FAQs) About Fake Windows 10 Updates
Q: How do I know if I have installed a fake Windows 10 update?
A: If you suspect you may have installed a fake update, scan your system with a reputable antivirus program. Look for suspicious files or processes, and monitor your system for unusual behavior. If you notice any signs of compromise, take immediate action to remove the malware and restore your system.
Q: Can I reverse the effects of a fake update?
A: Depending on the type of malware installed, you may be able to remove it and restore your system. Use a reputable antivirus program to scan your system and remove any malicious files. You may also need to restore your system to a previous backup or perform a clean installation of Windows 10.
Q: Is it safe to download updates from third-party websites?
A: It is generally not recommended to download updates from third-party websites. Stick to official sources like the Microsoft website or trusted software repositories.
Q: What should I do if I encounter a fake update notification?
A: If you encounter a suspicious update notification, do not click on any links or install any software. Contact Microsoft support for assistance and report the suspicious activity.
Tips for Avoiding Fake Windows 10 Updates
- Stay Informed: Keep yourself informed about the latest threats and vulnerabilities by reading security blogs, news articles, and official Microsoft advisories.
- Be Skeptical: Approach any unsolicited update notifications with caution. Do not blindly trust updates from unknown sources or those that appear too good to be true.
- Trust Your Instincts: If something feels suspicious, it probably is. Do not hesitate to seek help from trusted sources or professionals if you are unsure about an update.
Conclusion: Staying Safe in the Digital Age
Fake Windows 10 updates pose a significant threat to computer security and user privacy. By understanding how these deceptive tactics work, recognizing the warning signs, and implementing effective countermeasures, users can significantly reduce their risk of falling prey to these malicious schemes. Staying informed, exercising caution, and prioritizing cybersecurity practices are essential in navigating the ever-evolving digital landscape.





Closure
Thus, we hope this article has provided valuable insights into The Deceptive Allure of Fake Windows 10 Updates: A Comprehensive Guide to Protection. We thank you for taking the time to read this article. See you in our next article!