The Deceptive Allure of Fake Update Windows: Understanding and Avoiding a Digital Threat
Related Articles: The Deceptive Allure of Fake Update Windows: Understanding and Avoiding a Digital Threat
Introduction
With great pleasure, we will explore the intriguing topic related to The Deceptive Allure of Fake Update Windows: Understanding and Avoiding a Digital Threat. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: The Deceptive Allure of Fake Update Windows: Understanding and Avoiding a Digital Threat
- 2 Introduction
- 3 The Deceptive Allure of Fake Update Windows: Understanding and Avoiding a Digital Threat
- 3.1 Understanding the Deception: How Fake Update Windows Work
- 3.2 Recognizing the Red Flags: Identifying Fake Update Windows
- 3.3 Shielding Your System: Mitigation Strategies Against Fake Update Windows
- 3.4 FAQs about Fake Update Windows
- 3.5 Tips for Avoiding Fake Update Windows
- 3.6 Conclusion: Staying Vigilant in a Digital World
- 4 Closure
The Deceptive Allure of Fake Update Windows: Understanding and Avoiding a Digital Threat

In the contemporary digital landscape, where software updates are paramount for security and functionality, malicious actors have devised a cunning tactic to exploit user trust: fake update windows. These deceptive interfaces, often mimicking legitimate update prompts, lure unsuspecting users into compromising their systems, exposing them to data theft, malware infection, and other cyber threats. This article provides a comprehensive understanding of fake update windows, exploring their mechanisms, identifying their telltale signs, and outlining strategies to mitigate their risks.
Understanding the Deception: How Fake Update Windows Work
Fake update windows, also known as "fake update scams," are a form of social engineering, leveraging psychological manipulation to trick users into granting access to their systems. They typically operate through the following stages:
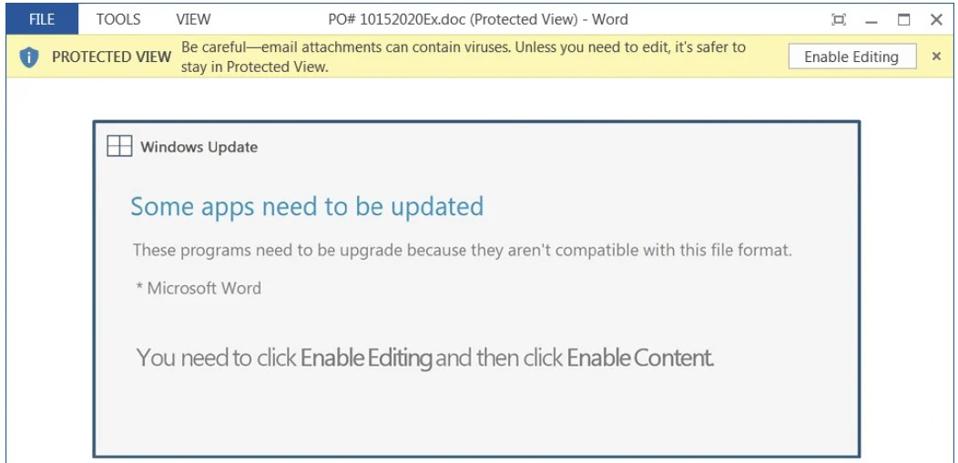
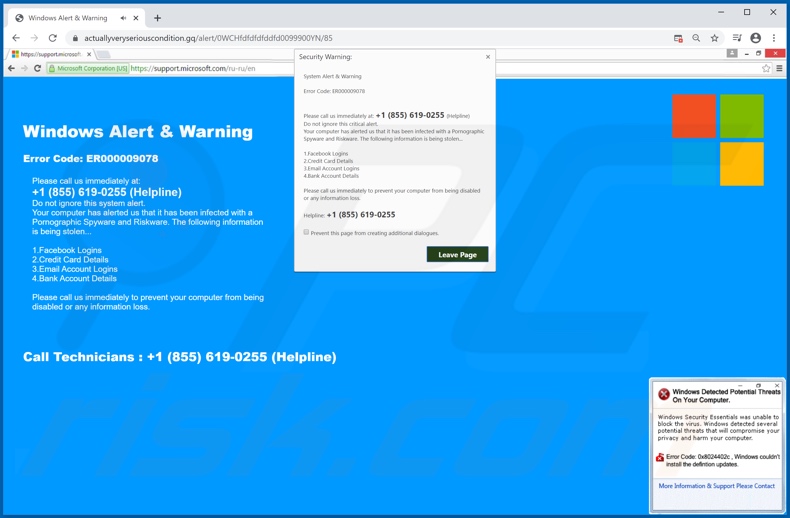
1. The Lure: Fake update windows often appear as pop-up messages, mimicking the design and language of legitimate software updates. They might display seemingly urgent messages, claiming critical security patches or software enhancements are available. These messages can be strategically timed to capitalize on users’ anxieties about vulnerabilities and their desire for a secure system.
2. The Hook: The deceptive window will usually contain a prominent "Update Now" or "Download" button. Clicking on this button triggers the malicious payload, which could be a malware installer, a phishing link, or a request for sensitive information.
3. The Compromise: Once the user interacts with the fake update window, their system becomes vulnerable. Malware can be downloaded and installed, granting attackers access to sensitive data, compromising system security, or even turning the device into a botnet participant.
Recognizing the Red Flags: Identifying Fake Update Windows
While fake update windows can be cleverly designed, certain clues can help users differentiate them from genuine update prompts. Here are key indicators to watch out for:
1. Mismatched Design: Pay close attention to the window’s appearance. Does it match the design and style of the software it claims to update? Fake update windows often have inconsistent fonts, colors, and layouts compared to legitimate updates.
2. Suspicious URLs: Before clicking on any links within the update window, carefully examine the URL. Does it look legitimate and match the expected domain name for the software? Fake update windows often employ disguised URLs or use shortened links that mask their true destination.
3. Urgent Tone and Pressure: Be wary of update messages that employ alarming language or create a sense of urgency. Legitimate software updates rarely employ fear tactics and typically provide clear instructions and explanations.
4. Missing Security Indicators: Genuine update windows often display security certificates or logos from reputable organizations like VeriSign or Norton. Fake update windows might lack these indicators or display fake certificates.
5. Unusual Installation Behavior: Genuine software updates usually involve a straightforward installation process. Be suspicious if the update window requests unusual permissions, demands access to sensitive data, or attempts to install multiple programs at once.
Shielding Your System: Mitigation Strategies Against Fake Update Windows
Protecting your system from fake update windows requires a proactive approach, combining vigilance with security measures. Here are some effective strategies:
1. Stay Informed: Keep yourself updated on common online threats and scams. Research and familiarize yourself with the latest phishing techniques, malware trends, and common social engineering tactics.
2. Exercise Caution: Be skeptical of unsolicited update messages, especially those that appear unexpectedly or use aggressive language. Avoid clicking on suspicious links or downloading software from unknown sources.
3. Verify Software Updates: If you receive an update notification, verify its authenticity by visiting the official website of the software developer or checking for updates through your operating system’s update manager.
4. Install Security Software: Employ reputable antivirus and anti-malware software to protect your system from malicious downloads and infections. Ensure your security software is up-to-date and configured to scan all downloads and attachments.
5. Keep Your Software Updated: Regularly update your operating system, applications, and security software to patch vulnerabilities and strengthen your system’s defenses against known threats.
6. Enable Two-Factor Authentication: Implement two-factor authentication wherever possible to add an extra layer of security and prevent unauthorized access to your accounts.
7. Be Aware of Phishing Attempts: Phishing emails can be a common source of fake update windows. Be cautious of emails that request personal information, urge you to click on suspicious links, or claim to offer software updates.
8. Report Suspicious Activity: If you encounter a suspicious update window, report it to the appropriate authorities or software developer. This helps raise awareness and prevent others from falling victim to the same scam.
FAQs about Fake Update Windows
1. Can I trust update windows that appear in my browser?
While legitimate software updates can sometimes appear in your browser, it’s essential to exercise caution. Always verify the source of the update and the URL before clicking on any links.
2. What should I do if I accidentally click on a fake update window?
If you suspect you’ve clicked on a fake update window, immediately disconnect from the internet to prevent further infection. Run a full system scan with your antivirus software and consider resetting your browser to its default settings.
3. How can I tell if an update is legitimate?
Legitimate updates typically come from trusted sources, such as the official website of the software developer or your operating system’s update manager. They usually have a consistent design and language, and they don’t employ alarming or manipulative tactics.
4. Are fake update windows a serious threat?
Yes, fake update windows can be a significant threat to your system security. They can lead to malware infections, data theft, and other cyber crimes. It’s crucial to be aware of these threats and take proactive measures to protect yourself.
5. How often do fake update windows appear?
The frequency of fake update windows can vary depending on current cybercrime trends and user vulnerabilities. However, they remain a persistent threat, requiring ongoing vigilance and security measures.
Tips for Avoiding Fake Update Windows
1. Be Skeptical: Don’t blindly trust unsolicited update messages, especially those that appear unexpectedly or use aggressive language.
2. Verify Sources: Always verify the source of an update by checking the official website of the software developer or your operating system’s update manager.
3. Use Reputable Software: Download software only from trusted sources and avoid using cracked or pirated versions, which are often bundled with malware.
4. Keep Software Updated: Regularly update your operating system, applications, and security software to patch vulnerabilities and strengthen your system’s defenses.
5. Be Aware of Phishing: Be cautious of emails that request personal information, urge you to click on suspicious links, or claim to offer software updates.
Conclusion: Staying Vigilant in a Digital World
Fake update windows are a persistent threat, exploiting user trust and vulnerability. By understanding their mechanisms, recognizing their telltale signs, and implementing proactive mitigation strategies, users can effectively protect themselves from these deceptive tactics. Staying informed, exercising caution, and maintaining a healthy skepticism are crucial elements in navigating the ever-evolving digital landscape. Remember, vigilance is the key to safeguarding your system and personal data from the ever-present dangers of cyber threats.
![]()
![]()
![]()
![]()
![]()
![]()
Closure
Thus, we hope this article has provided valuable insights into The Deceptive Allure of Fake Update Windows: Understanding and Avoiding a Digital Threat. We hope you find this article informative and beneficial. See you in our next article!